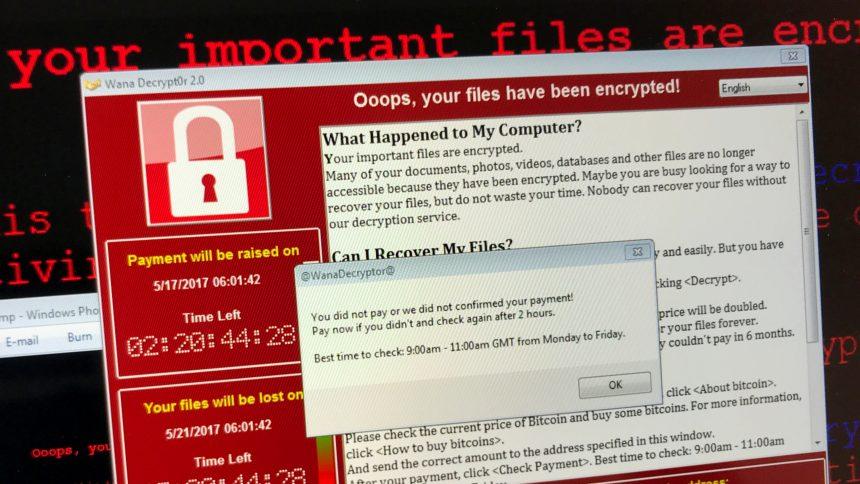
Ransomware attacks continue to be a significant threat in the digital landscape, and X101 is among the latest to surface. This ransomware is particularly dangerous as it encrypts victims’ files, demands a ransom for their release, and has the potential to cause irreparable damage. In this article, we will explore the details of the X101 ransomware, its method of operation, and the steps you can take to remove it and prevent future infections.
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!
What Is X101 Ransomware?
X101 ransomware is a type of malware that encrypts files on infected systems, rendering them inaccessible without a decryption key. Discovered through samples submitted to VirusTotal, this ransomware is identified by its distinctive behaviors:
- File Encryption: X101 encrypts files using a strong encryption algorithm (TermCryptV101+RSA2048) and appends the “.X101” extension to each file. For example, “1.jpg” becomes “1.jpg.[8ce450cd67].X101”.
- Ransom Note: A text file named “!!!HOW_TO_DECRYPT!!!.TXT” is created, providing instructions to victims.
The Ransom Note Details
The ransom note informs victims that their files have been encrypted and claims recovery is impossible without purchasing a special decryption key. Victims are asked to pay $250 in Bitcoin to a provided wallet address. Contact details for the attackers include a Telegram handle (@t1000rn) and a Jabber ID (t1000rn@404.city). The note warns against:
- Renaming encrypted files.
- Using third-party decryption tools.
- Seeking help from data recovery services.
The attackers also offer to decrypt one file for free as proof of their capabilities.
Detection Names
X101 ransomware is identified under various names by popular antivirus tools:
- Avast: Win32:RansomX-gen [Ransom]
- Combo Cleaner: Dump:Generic.Ransom.Spora.E9C29B2F
- ESET-NOD32: A Variant Of Win32/Filecoder.NSF
- Kaspersky: HEUR:Trojan-Ransom.Win32.Generic
- Microsoft: Ransom:Win32/MedusaLocker.A!MTB
How X101 Ransomware Spreads
Cybercriminals use numerous methods to distribute ransomware like X101, including:
- Malicious Emails: Attachments containing macros or links to infected websites.
- Pirated Software: Cracking tools, key generators, and unauthorized downloads.
- Exploiting Security Vulnerabilities: Flaws in outdated operating systems and applications.
- Malicious Ads: Fake advertisements leading to infected downloads.
- Compromised Websites: Hosting malware disguised as legitimate software.
- USB Drives: Spreading malware through infected storage devices.
Symptoms of X101 Ransomware Infection
Victims of X101 ransomware may notice the following symptoms:
- Files become inaccessible, with a new extension (“.X101”) appended to their names.
- The appearance of a ransom note (“!!!HOW_TO_DECRYPT!!!.TXT”) on the desktop or in affected folders.
- Inability to open previously functional files.
- Demands for Bitcoin payment to unlock files.
Consequences of Paying the Ransom
Paying the ransom is highly discouraged for several reasons:
- No Guarantee of Recovery: Cybercriminals may not provide the decryption key even after payment.
- Encourages Further Attacks: Paying the ransom funds future criminal activities.
- Data Theft Risks: Ransomware often comes bundled with other malware, such as password-stealing trojans.
How to Remove X101 Ransomware
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!
To eliminate X101 ransomware and prevent further damage, follow these steps:
Step 1: Isolate the Infected Device
Immediately disconnect the infected device from the internet and any connected networks. This prevents the malware from spreading to other devices.
Step 2: Use Safe Mode
Boot your computer in Safe Mode to disable any active ransomware processes:
- Restart your computer.
- Press F8 (or the appropriate key for your system) during boot-up.
- Select “Safe Mode with Networking.”
Step 3: Install and Run SpyHunter
SpyHunter is a reliable anti-malware tool designed to detect and remove ransomware like X101. Here’s how to use it:
- Download SpyHunter.
- Install the software and perform a full system scan.
- Allow SpyHunter to detect and quarantine X101 ransomware.
- Follow the on-screen instructions to remove the malware completely.
Step 4: Restore Files (If Possible)
If you have backups, use them to restore your files after removing the ransomware. If no backups are available, consider using reputable third-party file recovery tools. Avoid using unverified decryption tools, as they may further damage your data.
Preventing Future Ransomware Infections
To protect your system from ransomware attacks, implement the following preventive measures:
Regular Backups
- Maintain up-to-date backups of important data.
- Store backups on offline or cloud-based storage systems.
Keep Software Updated
Install updates for your operating system, antivirus software, and applications to patch security vulnerabilities.
Use Antivirus Protection
Employ a robust antivirus program like SpyHunter for real-time protection against ransomware and other threats.
Avoid Suspicious Emails
Do not open attachments or click on links from unknown or suspicious senders.
Download Software from Official Sources
Avoid pirated software, cracking tools, and unauthorized downloads.
Enable Firewall and Network Security
- Use a firewall to block unauthorized access to your system.
- Employ network security solutions to monitor and prevent threats.
Educate Yourself and Your Team
Stay informed about the latest cybersecurity threats and share knowledge with others.
Conclusion
X101 ransomware poses a serious threat to individuals and organizations alike. Its ability to encrypt files and demand payment can lead to significant data loss and financial damage. Removing the ransomware using a tool like SpyHunter and following best practices for prevention are essential steps in combating this malware. By staying vigilant and implementing robust security measures, you can reduce the risk of falling victim to ransomware attacks.
Text Presented in X101 Ransomware’s Text File
###################################################
########### You became victim of the .X101 Ransomware-Virus #############
###################################################
## MachineID: 530907702X and LaunchID: 8ce450cd67 ##
###################################################
## The harddisks of your computer have been encrypted with an military grade ##
## encryption algorithm TermCryptV101+RSA2048.
## There is no way to restore your data without a special key. ##
###################################################
###################################################
##To decrypt the files, you need to pay 250 USD in bitcoins to the BTC wallet##
below,then after 1 confirmation of the bitcoin network, ##
>>>>you can get the decryptor by writing to the following contact contacts!<<<<
## ————————————————————————–##
## BTC Wallet – 37kbnNTyBv8hNHwVX1CJQTrnXgKkh4jbZu ##
## ————————————————————————–##
## Exchangers for exchanging !!!!for cryptocurrency: !!!
## >>> hxxps://www.bestchange.net <<<
## If you want to decrypt your files, you have to get RSA private key.
## After the successful payment and decrypting your files, we will give
## you FULL instructions HOW to IMPROVE your security system.
## TELEGRAM us: >> @t1000rn <<
## Jabber: >> t1000rn@404.city FULL ONLINE <<
‘Do not rename encrypted files.
‘Do not try to decrypt your data using third party software,
‘it may cause permanent data loss.
‘Do not try to decrypt your data using third party software,
‘it may cause permanent data loss.
=====================================================
>>> Do not pay data recovery companies to get the key, they will email me! <<<
################## We ready to answer all your questions! #####################
>>>>>>>>>>>>>>>>> HOW to understand that we are NOT scammers?<<<<<<<<<<<<<<<<<<
######### You can ask SUPPORT for the TEST-decryption for ONE file ! ###########