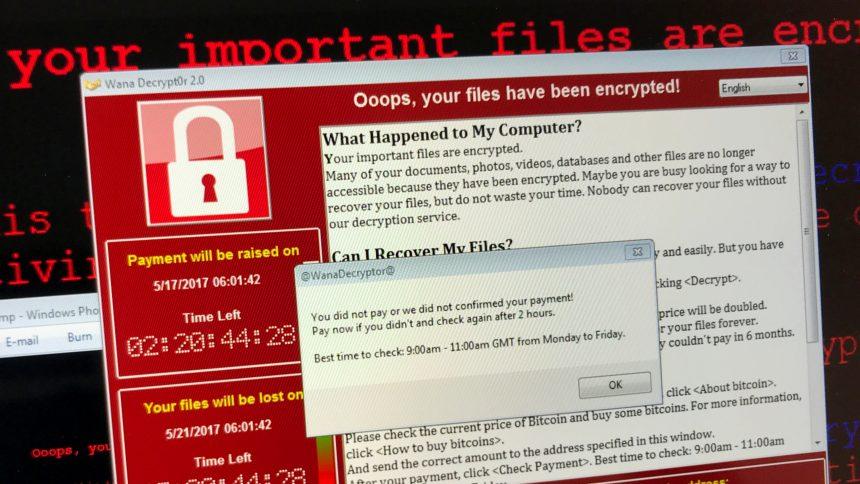
Hyena ransomware, a member of the MedusaLocker family, is a dangerous malware strain that encrypts files and demands payment for decryption. This malicious software not only targets individuals but also poses a significant threat to businesses by encrypting critical data and threatening to release confidential information.
Threat Summary
| Attribute | Details |
|---|---|
| Name | Hyena Ransomware |
| Threat Type | Ransomware, Crypto Virus, Files Locker |
| Encrypted File Extension | .hyena111 |
| Ransom Note File | READ_NOTE.html |
| Free Decryptor Available? | No |
| Cybercriminal Contact | pomocit02@kanzensei.top, pomocit02@surakshaguardian.com, Tor website |
| Detection Names | Avast (Win64:RansomX-gen [Ransom]), Combo Cleaner (Gen:Variant.Lazy.633339), ESET-NOD32 (A Variant Of Win64/Filecoder.MedusaLocker.A), Kaspersky (HEUR:Trojan-Ransom.Win32.Generic), Microsoft (Ransom:Win64/MedusaLocker) |
| Symptoms | Files are inaccessible and have a .hyena111 extension. A ransom note is displayed, and payment is demanded in Bitcoin. |
| Damage | Encrypts files, potential for data leaks, installation of additional malware, financial loss. |
| Distribution Methods | Infected email attachments (macros), torrent websites, malicious ads, unpatched software vulnerabilities. |
| Danger Level | High |
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!
Overview of Hyena Ransomware
Hyena ransomware encrypts files using a combination of RSA and AES encryption algorithms. It renames files by appending the .hyena111 extension (e.g., document.docx becomes document.docx.hyena111). Victims are presented with a ransom note (READ_NOTE.html), which outlines the demands and consequences. The note emphasizes that decryption is only possible through the attackers and warns against using third-party tools, claiming they could permanently corrupt the files.
Ransom Note Content
The ransom note highlights the following:
- All files have been encrypted, and confidential data has been stolen.
- Victims can send 2-3 files for free decryption as proof of decryption capabilities.
- Payment is required in Bitcoin, with a price increase after 72 hours.
- Failure to pay results in data leakage or resale.
Removal Guide for Hyena Ransomware
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!
Step 1: Isolate the Infected System
- Disconnect the infected device from the internet to prevent further data leaks or malware downloads.
- Disconnect any connected external drives or networked devices.
Step 2: Use Safe Mode with Networking
Restart your computer and enter Safe Mode with Networking:
- For Windows: Restart and press
F8(or relevant key) before the Windows logo appears. - Select Safe Mode with Networking from the options.
Step 3: Install and Run SpyHunter
- Download SpyHunter.
- Transfer the installer to the infected system using a USB drive.
- Install SpyHunter and perform a full system scan.
- Follow the on-screen instructions to remove all detected threats, including Hyena ransomware.
Step 4: Recover Encrypted Files
- Restore files from backups if available.
- If no backups exist, consult trusted cybersecurity experts to explore possible decryption tools or recovery methods.
Step 5: Clean Up and Update System
- Ensure your operating system and software are updated to patch vulnerabilities.
- Enable firewall and antivirus protection.
Preventive Measures
To minimize the risk of ransomware attacks in the future, enforce the following practices:
- Regular Backups:
- Maintain frequent backups of critical data on external drives or cloud services.
- Ensure backups are stored offline or in secure environments.
- Email Caution:
- Avoid opening attachments or clicking links in suspicious emails.
- Verify the sender’s authenticity before engaging.
- Use Reliable Security Software:
- Install a trusted antivirus solution like SpyHunter to monitor and protect your system.
- Enable real-time threat detection.
- Update Software Regularly: Keep your operating system, software, and security tools updated to patch vulnerabilities.
- Avoid Untrusted Sources:
- Do not download software, files, or media from unverified websites or P2P networks.
- Avoid using pirated software and key generators.
- Enable Network Security: Use firewalls and VPNs to secure your network from unauthorized access.
Why Use SpyHunter?
SpyHunter is a powerful anti-malware tool designed to detect and remove advanced threats like Hyena ransomware. Its features include:
- Real-time protection against malware, ransomware, and spyware.
- Advanced scanning technology to identify hidden threats.
- User-friendly interface and 24/7 customer support.
By understanding the threat posed by Hyena ransomware and following these steps, you can safeguard your data and minimize potential damages. Stay vigilant and proactive in your cybersecurity measures to combat evolving threats.
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!