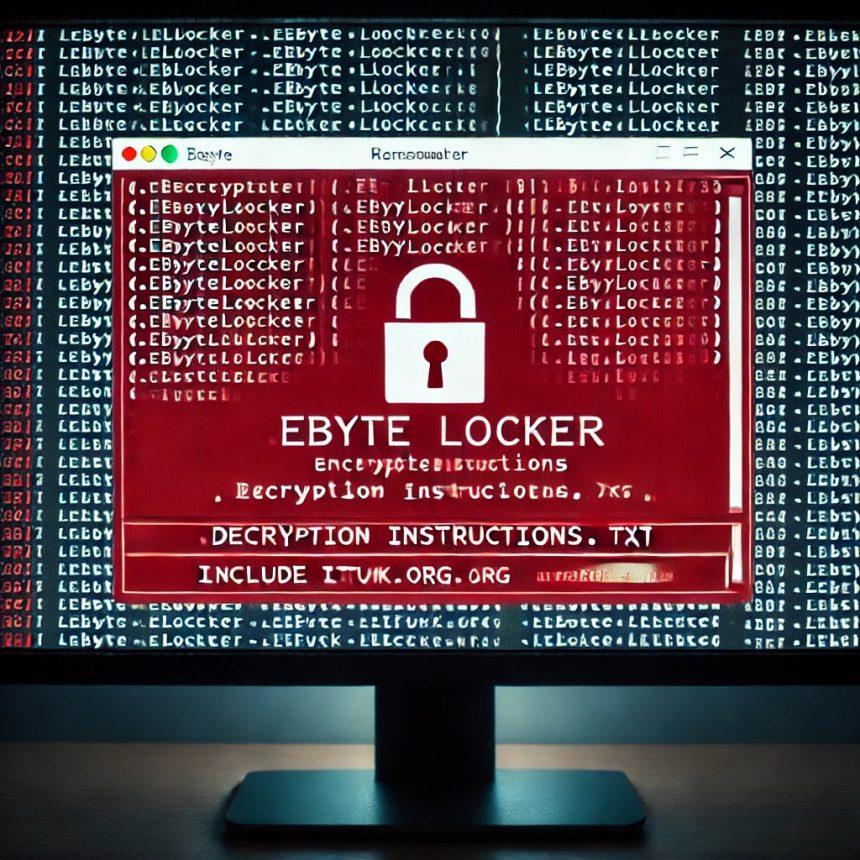
What Is EByte Locker Ransomware?
EByte Locker is a malicious ransomware strain based on the Prince ransomware family. It encrypts files on the victim’s computer and appends the “.EByteLocker” extension to them. Once encryption is complete, it changes the desktop wallpaper and creates a ransom note titled “Decryption Instructions.txt,” instructing victims on how to recover their files—usually by paying a cryptocurrency ransom.
This ransomware poses a severe threat, not just by locking critical files but also by potentially spreading across networks, making the attack even more damaging.
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!
Threat Summary
| Attribute | Details |
|---|---|
| Threat Type | Ransomware, Crypto Virus, File Locker |
| Encrypted File Extension | .EByteLocker |
| Ransom Note File Name | Decryption Instructions.txt |
| Associated Email Address | example@airmail.cc |
| Detection Names | Avast (Win64:Malware-gen), Combo Cleaner (Generic.Ransom.Prince.A.F6533D94), Microsoft (Ransom:Win64/PrinceRansom.YAA!MTB) |
| Symptoms of Infection | Files are inaccessible, files renamed with .EByteLocker, ransom note on the desktop, altered wallpaper |
| Damage | Files encrypted and unrecoverable without a decryption key, potential additional malware infections |
| Distribution Methods | Infected email attachments, malicious ads, compromised websites, pirated software, unpatched vulnerabilities |
| Danger Level | Severe |
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!
How EByte Locker Operates
File Encryption
EByte Locker encrypts files using strong cryptographic algorithms, making them inaccessible without a unique decryption key. During the encryption process, the malware renames files by appending the “.EByteLocker” extension. For example:
photo.jpgbecomesphoto.jpg.EByteLockerdocument.pdfbecomesdocument.pdf.EByteLocker
Ransom Note
The ransom note, titled “Decryption Instructions.txt”, contains the following information:
- Notification of encryption.
- Instructions to avoid modifying encrypted files to prevent permanent damage.
- Directions to contact the attackers at
example@airmail.ccfor ransom payment details, typically in cryptocurrency.
Danger of Paying the Ransom
Paying the ransom does not guarantee file recovery. Many victims report that attackers do not provide a decryption key even after payment. Thus, alternative recovery options should be prioritized.
How Does EByte Locker Spread?
EByte Locker uses various methods to infiltrate devices:
- Malicious Email Attachments: Emails with infected attachments (e.g., Word documents with macros or PDF files).
- Compromised Websites: Visiting websites embedded with malicious scripts.
- Pirated Software: Downloading cracked software or key generators.
- Unpatched Vulnerabilities: Exploiting outdated operating systems or applications.
- Malicious Ads and Pop-Ups: Clicking deceptive ads that lead to malware downloads.
These distribution methods are designed to trick users into unknowingly executing the ransomware.
Removing EByte Locker?
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!
Removing ransomware like EByte Locker requires immediate action to prevent further damage. Here’s a step-by-step guide:
Disconnect from the Internet
Isolate the infected device by disconnecting it from the internet to prevent the ransomware from spreading to other devices.
Use SpyHunter to Remove EByte Locker
SpyHunter is a powerful anti-malware tool capable of identifying and removing ransomware threats. Follow these steps:
- Step 1: Download and install SpyHunter.
- Step 2: Perform a full system scan to detect EByte Locker and any associated malware.
- Step 3: Remove all threats detected by SpyHunter.
- Step 4: Restart your computer and verify that the ransomware has been eliminated.
Restore Files
If you have backups, restore your files from them after removing the malware. In some cases, third-party decryption tools may be available. Research the availability of a tool specific to EByte Locker online.
Preventive Measures to Avoid Future Ransomware Infections
Regular Backups
Maintain regular backups of critical files on an external device or secure cloud storage. Ensure that the backup system is not constantly connected to your computer.
Email Safety
Avoid opening unsolicited emails or attachments. Always verify the sender before interacting with email content.
Keep Software Updated
Regularly update your operating system, applications, and antivirus software to patch vulnerabilities.
Use Strong Security Tools
Install and use reputable anti-malware software like SpyHunter to protect against ransomware and other malware.
Avoid Untrusted Sources
Refrain from downloading software or media files from P2P networks, torrent websites, or third-party platforms.
Network Security
Secure your network by using a firewall and strong passwords. Disable unnecessary file-sharing features.
Remove annoying malware threats like this one in seconds!
Scan Your Computer for Free with SpyHunter
Download SpyHunter now, and scan your computer for this and other cybersecurity threats for free!