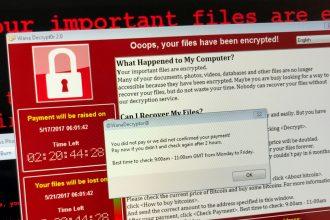
An In-Depth Look at Anomaly Ransomware: How to Protect Yourself
Anomaly ransomware, a dangerous variant based on the Chaos ransomware family, has emerged as a significant threat to computer users…
LucKY_Gh0$t Ransomware: Understanding and Removing the Threat
LucKY_Gh0$t is a dangerous ransomware strain that has recently been gaining attention for its sophisticated encryption techniques and its ties…
Aptlock Ransomware: A Threat Analysis and Removal Guide
Ransomware attacks continue to pose significant threats to businesses and individuals, with Aptlock being a recent and alarming addition to…
How to Deal with FunkLocker (FunkSec) Ransomware?
FunkLocker, also known as FunkSec, is a dangerous and highly disruptive type of ransomware that encrypts your files and demands…
Contacto Ransomware: A Detailed Overview and Removal Guide
Contacto ransomware is a malicious program that encrypts users’ files and demands a ransom for their decryption. This ransomware has…
YE1337 Ransomware: A Detailed Guide to Detection, Removal, and Prevention
Ransomware attacks have become one of the most significant threats to digital security, impacting individuals and businesses alike. One such…
Nitrogen Ransomware: Removal and Prevention
Nitrogen ransomware is a malicious software designed to encrypt files on infected systems, rendering them inaccessible without a decryption key.…
Bbuild Ransomware: Understanding, Removal, and Prevention
Ransomware remains one of the most destructive and costly cyber threats today, and one such notorious strain is Bbuild. Discovered…
RdpLocker Ransomware: Understanding, Removing, and Preventing Future Infections
RdpLocker is a sophisticated form of ransomware that targets personal and business data by encrypting files and demanding a ransom…
Held Ransomware Removal
Ransomware attacks continue to pose significant threats to individuals and organizations worldwide. One of the latest variants in the Djvu…