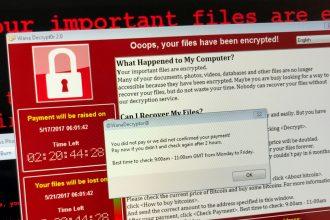
Hawk Ransomware: A Comprehensive Guide on Detection, Removal, and Prevention
Ransomware is a particularly devastating type of malware designed to encrypt users' files and demand payment for their release. Once…
VXUG Ransomware: A Comprehensive Guide on Removal and Prevention
Ransomware is a type of malicious software, or malware, designed to extort money from its victims by encrypting their files…
Green.exe Malware: Understanding, Consequences, and Removal
In today’s digital landscape, malware threats continue to evolve, posing significant risks to users worldwide. One such cyber threat is…
Colony Ransomware: A Comprehensive Threat Overview and Removal Guide
Ransomware is one of the most dangerous forms of malware, known for its ability to lock or encrypt a user’s…
SCRansom Ransomware: A Deep Dive into Ransomware Threats
Ransomware is a malicious form of software that encrypts a victim's files, rendering them inaccessible until a ransom is paid…
The RoxiApp Threat
In the world of cybersecurity, the term Potentially Unwanted Programs (PUPs) refers to software that may not be harmful in…
Kral Stealer: A Trojan Horse Malware Threat
Trojan horse malware, commonly referred to as "Trojans," is a type of malicious software that disguises itself as a legitimate…
NotLockBit Ransomware: A Comprehensive Overview
Ransomware is a form of malicious software (malware) designed to block access to a computer system or data until a…
Understanding Trojan Horse Malware: A Deep Dive into MultiVerze
Trojan horse malware, often referred to simply as "Trojans," is a type of malicious software that disguises itself as a…
PowerRat Trojan Horse Malware: A Deep Dive into Data Stealers and RATs
Trojan horse malware, commonly referred to as "Trojans," is a type of malicious software designed to infiltrate computer systems while…