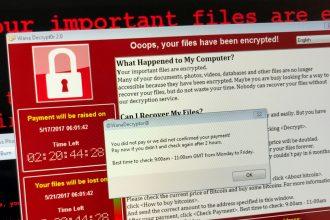
WebIndex Virus: Removal Guide and Prevention Tips
The WebIndex virus has emerged as a formidable cyber adversary, particularly targeting Mac systems. This insidious malware can infiltrate your…
Bestresulttostart.com Pop-up Redirects: How to Remove and Prevent Malicious Redirects
Malicious redirects stand out as a particularly insidious threat to safe web browsing. They hijack your browsing sessions, diverting you…
Namespace.pac_Exception_Code_261 Mac Cyber Threat
The emergence of new cyber threats is a constant concern for individuals and organizations alike. Among the latest adversaries lurking…
X-Finder Pro Malware: Removal Guide and Prevention Tips
A new menace has emerged, lurking in the shadows of the internet—X-Finder Pro malware. This insidious software infiltrates unsuspecting systems,…
OneHortensia.com Pop-up Virus: A Comprehensive Removal Guide
The threat of malware looms large, with cybercriminals constantly devising new methods to infiltrate and compromise systems. One such threat…
ConnectionCache.gqa: A Malware Threat Lurking in the Shadows of Your System
A new cyber menace has emerged, threatening the security and integrity of countless computer systems. This threat goes by the…
RinCrypt 3.0 Ransomware: A Menace in the Cyber Realm
RinCrypt 3.0 stands out, among its ilk, as a particularly insidious strain of ransomware, wreaking havoc on individuals and organizations…
Beware of the Invoice Request Email Scam: A Threat Overview
Cyber threats come in various forms, including lurking behind innocuous emails and seemingly legitimate requests. One such perilous scheme is…
Shinra Ransomware: Threat Analysis, Removal Guide, and Prevention Tips
The nuisance posed by ransomware remains a persistent menace, wreaking havoc on individuals and organizations alike. One such threat that…
Ghostly Stealer: A Stealthy Trojan, Stealing Your Digital Information
New threats to your digital privacy are constantly emerging, and among the latest is the Ghostly Stealer malware. This insidious…