“Error in the Mail Service” Phishing Scam: Combatting Spam Emails
Phishing scams are deceptive schemes designed to steal sensitive information by masquerading as legitimate entities. These scams often come in…
“Verify Delivery Error” Email Scam: Defending Agains Malicious Emails
Phishing scams have become increasingly sophisticated, preying on unsuspecting users through deceptive emails, messages, and websites. These scams are designed…
Inaszone.com Ads: The Constantly Growing Threat of Adware
Adware, short for advertising-supported software, is a type of malware designed to display or download advertising material, often without the…
Kneadspro.com Adware: A Growing Digital Threat
Adware, short for advertising-supported software, is a form of malware that inundates users with unwanted advertisements, often in the form…
Vattenfall AB Scam: Phishing Scams – A Dangerous Digital Threat
Phishing scams are a pervasive and malicious form of cyber attack that aim to deceive individuals into divulging sensitive information,…
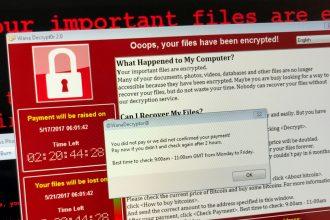
Griffin Ransomware: A Comprehensive Removal Guide
Ransomware is a form of malicious software (malware) that encrypts a victim’s files or locks them out of their system,…
Mailbox De-Activation Email Scam: A Comprehensive Guide to Identifying and Removing the Threat
Phishing scams have become an increasingly prevalent threat, designed to deceive unsuspecting individuals into revealing sensitive information or downloading malicious…
AttackNew Ransomware: Removing the Negative Effects of Encryption Malware
Ransomware is a type of malicious software designed to deny access to a computer system or files until a ransom…
Against Adobe Cloud Service Email Scams: Defending Against Online Scams
Phishing scams have become an increasingly prevalent threat. These scams are deceptive attempts to acquire sensitive information by masquerading as…
Hawk Eye Ransomware: A Comprehensive Overview
Ransomware is a form of malicious software designed to block access to a computer system or its files until a…