Microsoft Office 365 Password Notification Email Scam: Understanding the Threat of Phishing Scams
Phishing scams are among the most common and dangerous forms of cyber threats in the digital world. These attacks typically…
Cleandiskpc.com Ads: Understanding the Threat of Adware
Adware, short for advertising-supported software, is a type of malware designed to display unwanted advertisements on a user's computer. Unlike…
Beenbit Scam Removal
Cyber threats have become increasingly sophisticated, targeting users' personal information and system integrity. One such threat is the Beenbit Scam,…
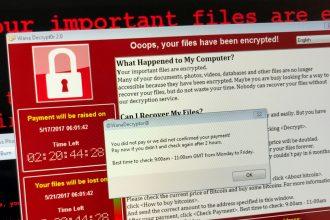
EDRKillShift Ransomware: A Comprehensive Removal Guide
Ransomware is a notorious form of malware designed to encrypt a user's files and demand a ransom for their release.…
Protectio7 Browser Extension Malware
The proliferation of malware is a significant concern for computer users worldwide. One such threat is the Protectio7 browser extension,…
AiSearchs Browser Extension Malware
AiSearchs is a browser extension that disguises itself as a legitimate tool, but in reality, it falls under the category…
Rdanger Ransomware: A Threat to Your System’s Health
Ransomware is a form of malicious software designed to block access to a computer system or encrypt the data stored…
SystemRecord Adware: A Common Cyber Threat
Adware, short for "advertising-supported software," is a form of malware designed to display unwanted advertisements on a user’s computer or…
H0rus Ransomware: A Growing Threat
Ransomware is a type of malicious software (malware) that cybercriminals use to extort money from victims by encrypting their files…
ModuleUpdater Adware and Its Impact on Your System
Adware is a type of malicious software that is designed to deliver unwanted advertisements to your computer. These ads often…