How to Detect, Remove, and Prevent RecordTransaction Adware on Mac Devices
Adware remains a persistent threat to internet users, exploiting vulnerabilities to deliver intrusive advertisements and compromise user privacy. RecordTransaction is…
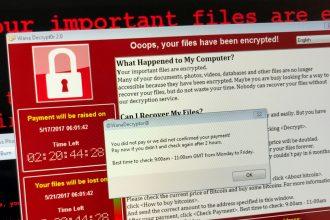
Hyena Ransomware: Analysis and Removal Guide
Hyena ransomware, a member of the MedusaLocker family, is a dangerous malware strain that encrypts files and demands payment for…
Enhancedefense[.]com Scam: What You Need to Know and How to Protect Yourself
Enhancedefensecom is a deceptive website that employs fake security alerts, pop-up ads, and intrusive notifications to manipulate users into interacting…
ProjectSet Adware: A Threat Overview and Removal Guide
The ProjectSet application, identified as part of the AdLoad malware family, is a deceptive adware program that jeopardizes the integrity…
WeRus Ransomware: Threat and Its Removal
Ransomware has become a significant menace in the digital world, with the WeRus ransomware standing out as a recent and…
Vulakingliter.com Browser Hijacker: Risks, Removal, and Prevention
Vulakingliter.com is a domain associated with the streaming platform Lookmovie.lol, which raises significant concerns regarding potential security risks. Visitors to…
Removing WantToCry Ransomware and Preventing Future Infections
Ransomware attacks are among the most destructive cyber threats faced by individuals and organizations. The WantToCry ransomware exemplifies this danger,…
Virus:Win32/Virut: Removal Guide
Virus:Win32/Virut is a highly dangerous trojan malware designed to infiltrate systems, steal sensitive data, and utilize resources for illicit activities…
opdomain22[.]online: Removal Guide & Prevention Tips
opdomain22online is a deceptive website designed to promote scams and expose users to potential malware threats. It lures unsuspecting users…
Mobitera[.]online: Detection, Removal, and Prevention
The internet is full of deceptive websites aiming to exploit users for financial gain or to infiltrate devices with harmful…