innok Ransomware: Analyzing the Threat and How to Remove It
Ransomware remains one of the most pervasive cyber threats, and innok ransomware…
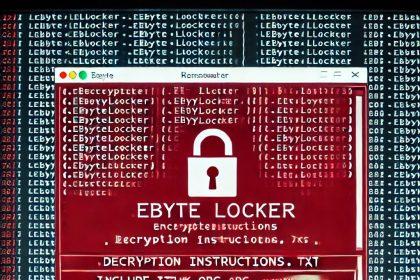
EByte Locker Ransomware: A Detailed Guide to Understanding, Removing, and Preventing This Threat
What Is EByte Locker Ransomware? EByte Locker is a malicious ransomware strain…
Spring Ransomware: Understanding and Removal
Spring ransomware is a malicious program based on the CONTI ransomware family,…
Why Managed Detection and Response (MDR) is a Game-Changer for Your Business
Let’s cut straight to the point: running a business today without a…
Disoaq App: Understanding the Threat and How to Remove It Safely
Potentially Unwanted Applications (PUAs) such as Disoaq App can have hazardous effects…
D0glun Ransomware – Threat Analysis and Removal Guide
Ransomware continues to evolve, with new threats like D0glun targeting unsuspecting users.…
Clone Ransomware: Understanding the Threat and How to Remove It Effectively
Clone ransomware is a member of the notorious Dharma ransomware family, identified…
Helldown Ransomware Removal
Helldown is an aggressive ransomware strain first identified in August 2024. It…
Trojan:BAT/Starter.G!Ink – What It Is, How to Remove It, and Prevention Tips
Trojan:BAT/Starter.G!Ink is a stealthy and highly dangerous malware that uses the Windows…