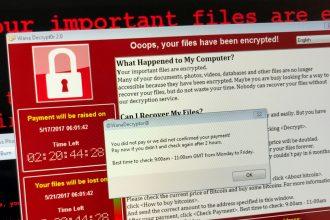
The MrBeast Ransomware: A Dangerous Threat to Your System and Data
Ransomware is a form of malicious software (malware) that targets the files and data of individuals or organizations. Once executed,…
Arcus Ransomware: A Removal Guide
Ransomware is a particularly dangerous type of malware that locks or encrypts files on an infected computer, demanding a ransom…
DarkSet Ransomware: Comprehensive Removal Guide and Prevention Tips
Ransomware is a severe form of malware that targets individuals and organizations by encrypting their data, then demanding a ransom…
How to Identify and Remove SpeedyLook Browser Hijacker: A Comprehensive Guide
Browser hijackers are a category of malware specifically designed to take control of a user’s internet browser, altering settings and…
RunningRAT Malware: Detailed Removal Guide & Prevention Tips
RunningRAT malware is a newly discovered Remote Access Trojan (RAT) that poses a severe risk to users by providing hackers…
Ymir Ransomware: A Guide on Detection, Prevention, and Removal
Ransomware is one of the most dangerous types of malware, designed to encrypt or lock users out of their own…
Ultra Button Adware: What It Is and How to Remove It Completely
Adware, short for "advertising-supported software," is a form of malware designed to bombard users with unwanted ads, disrupting their online…
SteelFox Trojan: Detection, Risks, and Comprehensive Removal Guide
SteelFox is one of these modern trojans, cleverly designed to bypass system defenses and silently execute malicious actions. Like many…
Detecting, Removing, and Preventing Elizarat Trojan Malware
Trojan horse malware, or simply “Trojans,” is a form of malicious software designed to appear as a legitimate program while…
Frag Ransomware Threat: Identification, Removal, and Prevention
Ransomware is a notorious form of malware designed to encrypt a victim’s files and demand a ransom payment in exchange…