Pro Video Downloader Adware: A Comprehensive Guide to Removal and Prevention
Pro Video Downloader may seem like a helpful solution to download videos in different formats and resolutions. However, there’s more…
ViT Ransomware: A Detailed Overview and Removal Guide
ViT is a dangerous form of ransomware belonging to the Xorist family. Discovered through the analysis of malware samples submitted…
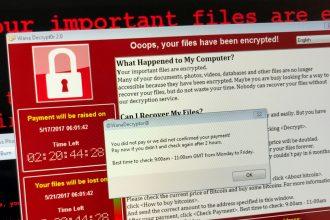
Revive Ransomware: How It Works, Removal Guide, and Prevention Tips
Ransomware attacks have been a significant cybersecurity threat for years, and the Revive ransomware is another addition to the growing…
MAGA Ransomware: How to Remove It and Prevent Future Infections
MAGA ransomware is a dangerous and persistent malware strain that belongs to the Dharma family of ransomware. It encrypts the…
Heur.AdvML.B: A Comprehensive Guide to Detection, Removal, and Prevention
Heur.AdvML.B is a heuristic detection name used by antivirus programs to flag potentially malicious files exhibiting suspicious behaviors that align…
WIN32/Offercore.b: A Dangerous PUP You Need to Remove Immediately
WIN32/Offercore.b is a potentially unwanted program (PUP) that poses a significant threat to your system. It is commonly detected by…
Claim Strategic Bitcoin Reserve Scam: Protecting Your Crypto Assets from Fraudulent Tactics
The digital world offers countless opportunities for investment, particularly in the ever-evolving cryptocurrency space. However, it also presents numerous risks,…
Rockstar 2FA PhaaS Toolkit: A Growing Threat to Cybersecurity and How to Protect Yourself
In today's increasingly interconnected world, cybersecurity threats continue to evolve and adapt to bypass traditional security measures. One such emerging…
Viruses Have Been Detected On Your Phone: A Dangerous Scam You Need to Avoid
The "Viruses Have Been Detected On Your Phone" scam is a classic example of phishing and social engineering tactics designed…
Yourbrolink3d.com Ads Virus: How to Identify and Remove It Effectively
Yourbrolink3d.com is a notorious online threat that falls under the category of browser hijackers and potentially unwanted programs (PUPs). It…