What Is MicroCoordinator and How to Remove It from Your Mac
Adware threats like MicroCoordinator are becoming increasingly common, especially for users of Mac systems. While Macs are known for their…
Adblock Bear: What You Need to Know and How to Remove It Effectively
The digital world is brimming with threats disguised as helpful tools, and Adblock Bear is a prime example. While it…
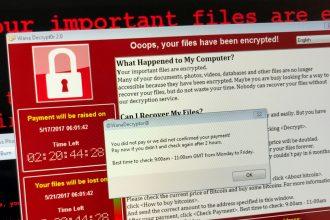
X101 Ransomware Threat and How to Remove It
Ransomware attacks continue to be a significant threat in the digital landscape, and X101 is among the latest to surface.…
Starcat Ransomware Threat
What Is Starcat Ransomware? Starcat is a dangerous ransomware strain designed to encrypt files on infected systems and extort victims…
Black (Prince) Ransomware Threat and How to Remove It
Ransomware attacks are a growing threat in the cybersecurity landscape, and the Black (Prince) ransomware is a malicious program designed…
“Qatar Airways” Email Scam: Protect Your Information and Finances
The rise in phishing campaigns continues to pose a significant threat to individuals and organizations worldwide. One such recent scam…
PlainGnome Malware: Threat Analysis and Removal Guide
PlainGnome is a sophisticated Android-specific spyware that emerged in 2024. This malicious software is designed to covertly record and steal…
BoneSpy: A Guide to the Android Spyware
What is BoneSpy? BoneSpy is a sophisticated Android spyware program that has been active since at least 2021. Rooted in…
Search-2go.com Browser Hijacker
Search-2go.com is a deceptive fake search engine that infiltrates users' web browsers through browser hijacking software. This type of software…
Search-Owl.com Browser Hijacker: A Detailed Guide and Removal Instructions
The world of cybersecurity is riddled with various types of malware, and one of the most persistent and irritating forms…