Protecting Your System from Win32/Sysupdate.gen!D
What Is Win32/Sysupdate.gen!D? Win32/Sysupdate.gen!D, also referred to as VirTool:Win32/Sysupdate.gen!D, is a detection label frequently flagged by security tools to denote…
Octagonfind.com Browser Hijacker
The internet is a space teeming with tools designed to enhance user experiences. Unfortunately, it is also home to numerous…
Unmasking the “LinkedIn Request To Buy From You” Scam
Phishing scams have become an unfortunate part of everyday online activity. One such threat currently making the rounds is the…
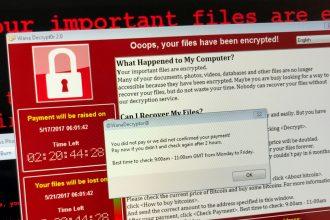
Nitrogen Ransomware: Removal and Prevention
Nitrogen ransomware is a malicious software designed to encrypt files on infected systems, rendering them inaccessible without a decryption key.…
Triund App Threat and How to Safeguard Your System
Unwanted applications like the Triund App often slip through the cracks, causing disruptions and endangering user data. Though it may…
MailCach Bitcoin Earning Scam: How It Works and How to Protect Yourself
Scams involving Bitcoin have surged in popularity, targeting unsuspecting individuals eager to profit from cryptocurrency. One such scam is the…
Ninja Browser: Threat It Poses and How to Remove It
Ninja Browser is an application that markets itself as an all-in-one downloader designed to enhance privacy while browsing the internet.…
Bbuild Ransomware: Understanding, Removal, and Prevention
Ransomware remains one of the most destructive and costly cyber threats today, and one such notorious strain is Bbuild. Discovered…
RdpLocker Ransomware: Understanding, Removing, and Preventing Future Infections
RdpLocker is a sophisticated form of ransomware that targets personal and business data by encrypting files and demanding a ransom…
Clickads-hub[.]top Threat: Detection, Removal, and Prevention
In today’s digital world, online threats continue to evolve, with a variety of tactics used to deceive users into unknowingly…