Rokinat.co.in: A Detailed Guide to Understanding, Removing, and Preventing This Online Threat
Rokinat.co.in is a potentially dangerous website that often appears on users' screens as part of an adware and browser hijacker…
Zula Games: Analysis and Removal Guide
The Free Games Virus, also known as Zula Games or Free Games 135, is a Potentially Unwanted Program (PUP) that…
DragonDrop Virus: Removal and Prevention
DragonDrop, typically known as a legitimate software tool aimed at enhancing file management through drag-and-drop functionality, has unfortunately also been…
Removing the “Zoho – Review Your Outgoing Emails” Scam
The "Zoho - Review Your Outgoing Emails" scam is a phishing attack disguised as a security notification from Zoho Mail.…
“Claim Inheritance Money” Email Scam: A Comprehensive Guide
Cybercriminals continue to innovate their methods, preying on unsuspecting victims with increasingly deceptive tactics. One such scam that has been…
Privacysearchapp.net: Browser Hijacker and Security Threat
Privacysearchapp.net, often flagged as a browser hijacker and potentially unwanted application (PUA), is a malicious extension that compromises user control…
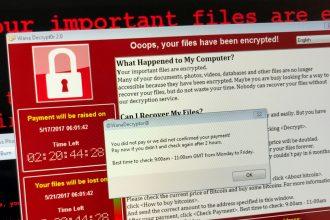
Annoy Ransomware: Comprehensive Removal Guide & Prevention Tips
Have your files been locked by the Annoy Ransomware virus? This insidious ransomware encrypts files and demands payment in cryptocurrency…
Removing Diagram.app Malware from macOS
Diagram.app is a suspicious application targeting macOS users. It belongs to the notorious Pirrit malware family, which is infamous for…
Nnice Ransomware: Analysis and Removal Guide
Nnice ransomware is a malicious program designed to encrypt files and extort victims by demanding payment for file decryption. This…
How to Remove Targetads-hub[.]top: The Complete Guide to Staying Safe Online
Overview of Targetads-hubtop Targetads-hubtop is a rogue webpage discovered during a routine inspection of suspicious websites. It aggressively promotes intrusive…