Suaiqi App – A Potentially Unwanted Application (PUA) Spreading Legion Loader Malware
The Suaiqi App is a Potentially Unwanted Application (PUA) that has been discovered within an installer distributed via rogue websites.…
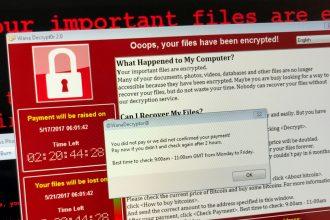
Core (Makop) Ransomware: A Guide to Removal and Prevention
Ransomware remains one of the most persistent and damaging cyber threats. One of the latest strains identified is Core (Makop)…
Brute Force Protection and Advanced Security Solutions: MDR, XDR, EPP, EDR, SIEM, and SOAR Explained
Picture this: A hacker sitting behind a keyboard, running automated scripts that guess passwords at lightning speed, hoping to break…
Suspicious Activity Monitoring in EDR: Strengthening Cybersecurity with Proactive Threat Detection
Imagine this: Your company’s network is running smoothly, your security team has all the latest tools, and yet—somewhere in the…
Microsoft Patches Critical Security Flaws in Azure AI Face Service and Microsoft Account
Threat Overview Microsoft has recently addressed two critical security vulnerabilities that posed potential threats to its cloud-based services. The security…
V (Dharma) Ransomware: Analysis and Removal Guide
Understanding V (Dharma) Ransomware V is a ransomware variant belonging to the notorious Dharma family, a well-known group of ransomware…
Altruistics Virus: A Dangerous Cryptojacking Trojan – Removal Guide and Prevention Tips
The Altruistics virus is a type of Trojan horse malware that infiltrates computers by disguising itself as legitimate software or…
BlackMoon Banking Trojan: A Dangerous Threat to Financial Security
BlackMoon, also known as KrBanker, is a banking Trojan that has been targeting online banking users since 2014. This malware…
Destiny Stealer Malware: A Dangerous Threat to Your Online Security
Cybercriminals continuously develop and distribute new threats that put users’ sensitive information at risk. One such advanced malware is Destiny…
LCRYPTX Ransomware: A Comprehensive Threat Analysis and Removal Guide
LCRYPTX is a ransomware-type malware that encrypts victims' files and demands a ransom for decryption. This cyber threat was recently…