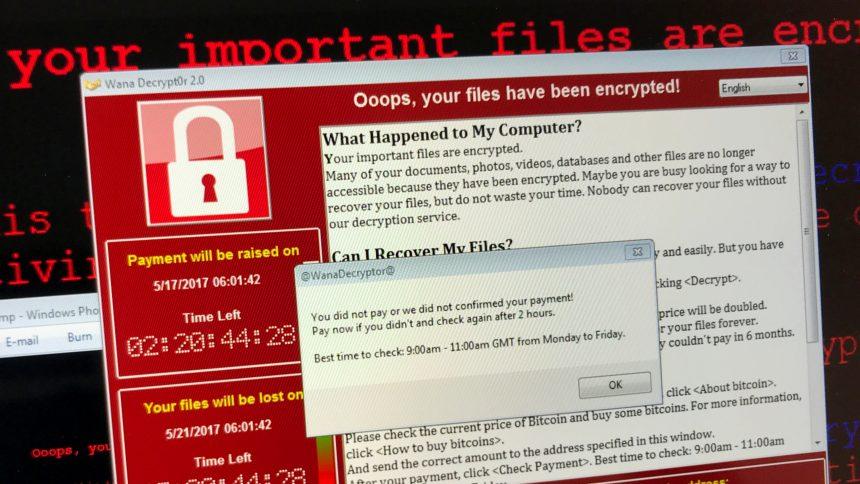
Ransomware is a notorious form of malware designed to encrypt a user’s files and demand a ransom for their release. This malicious software can render crucial files inaccessible, holding them hostage until the victim pays a specified amount. Ransomware attacks are increasingly common and pose a significant threat to both individuals and organizations. These attacks often exploit vulnerabilities in software, deceive users into opening malicious attachments, or leverage social engineering tactics to infiltrate systems.
EDRKillShift Ransomware: A Detailed Overview
One such threat is the EDRKillShift ransomware. Once installed on a system, this ransomware encrypts files and changes their extensions to prevent access. The primary function of EDRKillShift is to lock the victim’s files, thereby causing data loss and disruption. The ransomware uses sophisticated encryption algorithms to ensure that the files cannot be accessed without a decryption key, which the attackers only provide upon payment.
Installation and Actions
EDRKillShift typically infiltrates a system through phishing emails, malicious downloads, or software vulnerabilities. Once executed, it starts by encrypting various file types on the infected computer. It may append a specific file extension to encrypted files to indicate their status. For example, it could use a file extension like .edrshift. After encryption, EDRKillShift drops a ransom note on the infected system, usually in the form of a text file or an image.
Consequences and Ransom Note
The presence of EDRKillShift on a system has severe consequences. Victims will find that their files are no longer accessible and will encounter a ransom note demanding payment for the decryption key. The ransom note typically contains instructions on how to pay the ransom, which is often demanded in cryptocurrency like Bitcoin. It may also include threats to delete the encrypted files if the payment is not made within a specified timeframe.
Purpose and Threat
The primary goal of ransomware like EDRKillShift is financial gain. By encrypting valuable files and demanding a ransom, the attackers leverage the victim’s need to access their data for financial profit. This type of malware poses a serious threat as it can cause significant data loss and operational disruption, particularly for businesses that rely on digital files.
Symptoms of EDRKillShift Infection
Symptoms of an EDRKillShift infection include:
- Inaccessible Files: Files that cannot be opened or are displaying a new, unfamiliar file extension.
- Ransom Note: A file or message demanding payment for decryption.
- System Slowdown: General decrease in system performance due to the malware’s activities.
Detection Names
To determine if your system is infected with EDRKillShift, look for detection names such as:
- EDRKillShift Ransomware
- EDRShift Cryptovirus
- EDRShift Encrypter
Similar Threats
Other ransomware threats that you may encounter include:
- WannaCry: Known for its widespread impact and exploitation of vulnerabilities in Windows systems.
- Ryuk: Often targets large organizations and demands high ransoms.
- Sodinokibi (REvil): Known for its double extortion tactics, where data is both encrypted and threatened with public release.
Removal Guide
To remove EDRKillShift ransomware, follow these steps:
- Disconnect from the Internet: This prevents further communication with the ransomware’s command-and-control servers.
- Boot into Safe Mode: Restart your computer and press F8 or Shift + F8 to enter Safe Mode with Networking.
- Run an Anti-Malware Scan: Use a reputable anti-malware tool like SpyHunter to perform a full system scan. Download SpyHunter from here and install it.
- Quarantine or Remove the Malware: Follow the prompts in SpyHunter to quarantine or remove any detected threats.
- Restore Files from Backup: If you have backups, restore your files from a backup created before the infection.
- Change Passwords: Update all passwords, especially those related to online accounts that may have been accessed or compromised.
Preventive Measures
To avoid future ransomware attacks:
- Backup Regularly: Keep backups of important files in a secure, offline location.
- Use Updated Security Software: Install and regularly update anti-malware programs like SpyHunter.
- Avoid Suspicious Links: Be cautious of phishing emails and avoid clicking on unknown links or attachments.
- Keep Software Updated: Regularly update your operating system and applications to patch vulnerabilities.
Conclusion
Dealing with ransomware like EDRKillShift requires immediate action and vigilance. By following the removal guide and preventive measures outlined, you can mitigate the damage and protect your system from future threats. Download SpyHunter today to scan your computer for free and ensure it’s free from ransomware.
If you are still having trouble, consider contacting remote technical support options.