Tech News
Cyber Threats
How To Guides
Product Reviews
IT / Cybersecurity Best Practices
CVE-2024-48248: Critical NAKIVO Backup & Replication Flaw Actively Exploited—Patch Immediately
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has identified a severe…
How to Jailbreak DeepSeek: Unlocking AI Without Restrictions
DeepSeek is the latest AI chatbot making waves in the tech world.…
Microsoft Patches Critical Security Flaws in Azure AI Face Service and Microsoft Account
Threat Overview Microsoft has recently addressed two critical security vulnerabilities that posed…
Discover Categories
Latest News
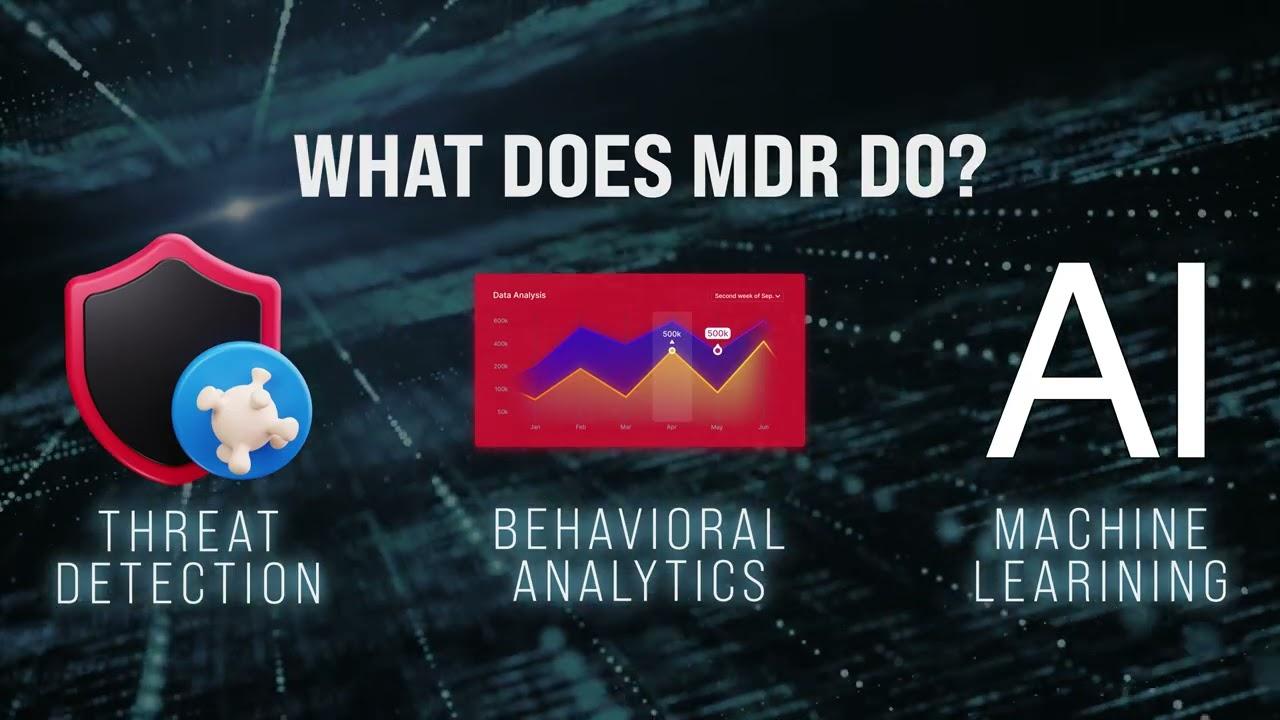
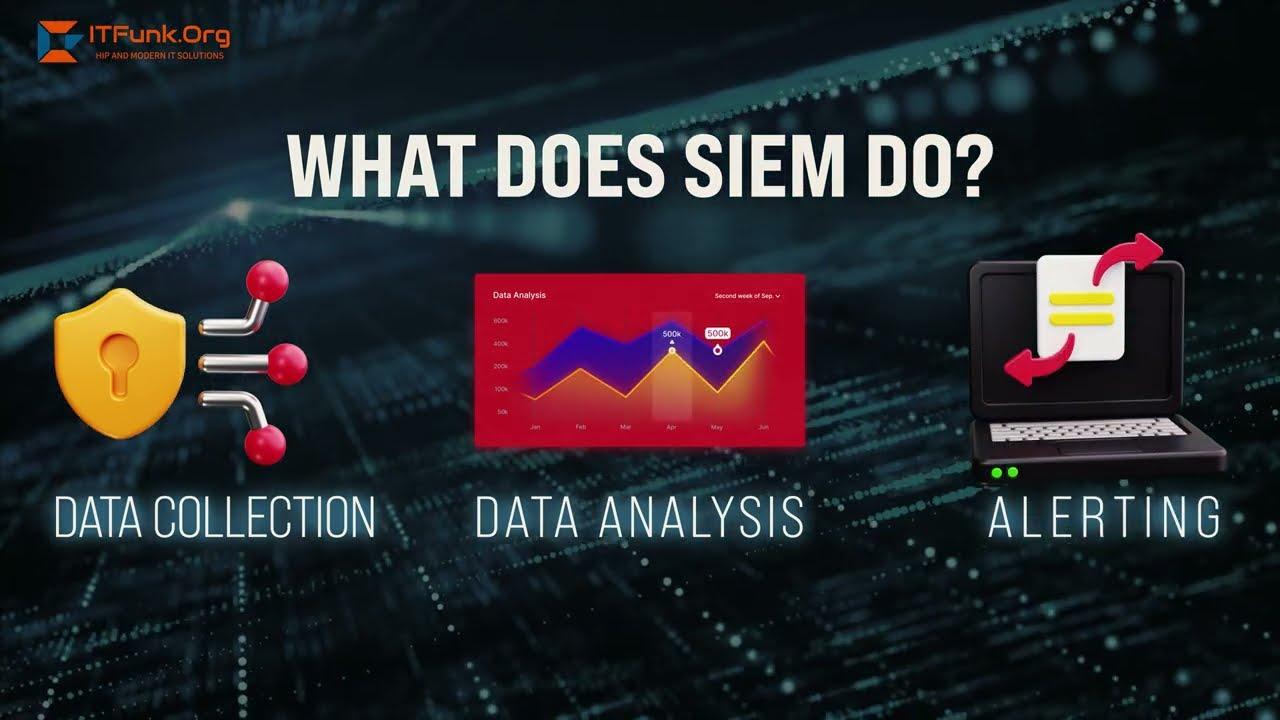
Mastering SIEM Implementation: Best Practices to Fortify Your Business Security
Let’s be real—the cyber threat landscape isn't getting any easier to manage. Attacks are smarter, faster, and more frequent. So…
How to Remove Chewbacca Ransomware
Chewbacca ransomware is a recently discovered crypto-malware threat that locks user files and demands a ransom payment to restore access.…
How to Remove Spectra Ransomware
Spectra ransomware is a malicious file-encrypting threat discovered through samples uploaded to the VirusTotal platform. It is based on the…
How to Deal With the “Two-Factor Authentication Activation” Email Scam
Cybercriminals are ramping up efforts to target cryptocurrency users with a deceptive new phishing campaign. The "Two-Factor Authentication Activation" email…
How to Deal With VoxFlowG USDT Airdrop Scam Email
Cybercriminals continue to exploit the popularity of cryptocurrency by deploying deceptive spam campaigns like the “VoxFlowG USDT Airdrop” scam. Disguised…
How to Remove ExpertComplete Adware From Your MAC
ExpertComplete is a deceptive application that has been classified as adware due to its primary function: flooding users with intrusive…
How to Deal With Ads by asyetaprovinc.org
The internet is riddled with deceptive websites designed to exploit unsuspecting users, and asyetaprovincorg is one such example. This rogue…


SCAN YOUR COMPUTER
Sponsored Content
ITFunk - Watch it